
Collect network information of others
WiFi sniffer, WiFi interceptor, Safe network.

WiFi sniffer, WiFi interceptor, Safe network.
Super Powerful WiFi Interceptor
Overview
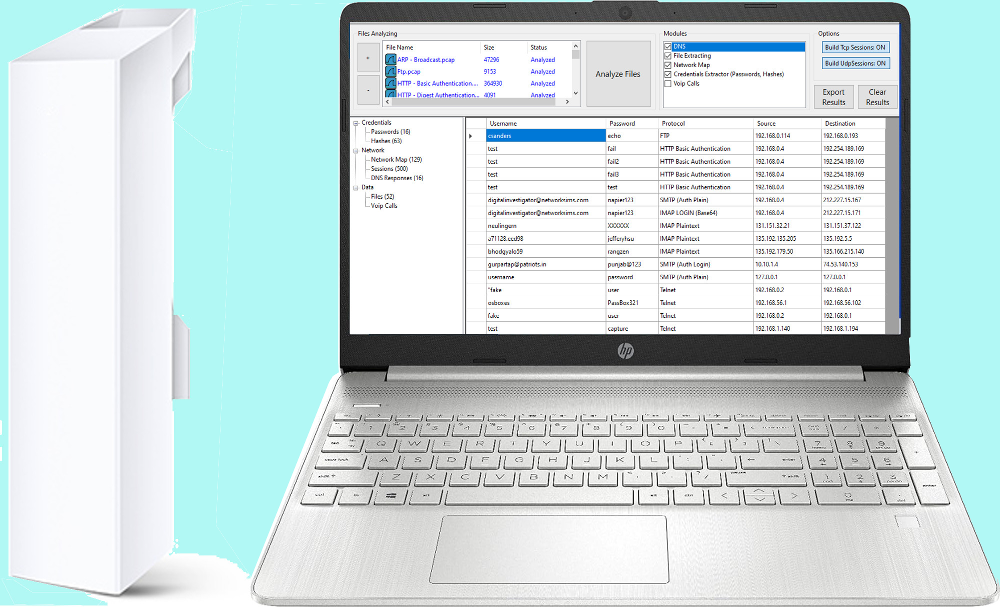
Powerful Wi-Fi Interception System is specifically developed for police operations and searching of information leaks in the office premises, government agencies and other structures where access to Wi-Fi networks is possible. The system consists of 2 main modules:
• Sniffer Module (Penetrator)
• Interception laptop (Interceptor)
The system can work either in Passive (monitoring) or Active modes. In monitoring mode, the operator can see ALL network users (working, connected, not connected) which are present within system coverage. The operator can create database of MAC addresses, signals levels, and all access points of users.
The system can also be configured as Wi-Fi Jammer or Wi-Fi Jamming Device to protect network privacy and security. Wi-Fi Jammer or Wi-Fi Jamming Device could transmit radio frequency signals and block the specified Wi-Fi connections, to keep sensitive information confidential or eliminate potential distractions in the workplace. Unpermitted laptops, cellular devices and other electronic devices could be blocked by Wi-Fi Jammer or Wi-Fi Jamming Device, to protect privacy. More importantly, Wi-Fi Jammer or Wi-Fi Jamming Device plays a key role in preventing hacking, information leakage and network breaches, as well as limiting unauthorized users from accessing important data.
Features
• Scanning for Wi-Fi stations and access points
• Capturing 802.11a, 802.11b, 802.11g and 802.11n WLAN traffic
• WEP or WPA/WPA2 keys specification to decrypt encrypted datas
• Display of detailed per-node and per-channel statistics
• Display of detailed IP connections statistics: IP addresses, ports, sessions, etc.
• Reconstruction of TCP sessions
Complete Set
• Sniffer Module (Penetrator)
• Interception laptop (Interceptor)
• Power Adaptor
• Set of Cables
• User Manual
Specifications
| Functions | Simultaneous monitoring of Wi-Fi networks | Up to 4 | ||
| Frequency band | 2.4GHz, 5GHz | |||
| Wi-Fi protocol | 802.11a/b/g/n | |||
| Wi-Fi security protocols | WEP, WPA-Personal, WPA2-Personal and WPA2-PSK | |||
| Jamming of Wi-Fi network | Yes | |||
| Interception of HTTPS/SSL sessions | Yes (MITM) | |||
| Coverage | Indoor | Up to 50 meters | ||
| Outdoor | Up to 100 meters and more | |||
| Internet content reconstruction | IMAP, POP3, SMTP | |||
| Webmail | Yahoo Mail, Gmail, Windows Live Hotmail, etc. | |||
| IM or Chat | Facebook Messager(Web), Yahoo Messenger, Gtalk, Yahoo Web Chat, Skype Voice Call Duration Log, etc. | |||
| HTTP | Web Link and Content, Reconstruct, Files Upload and Download, Video Streaming (Youtube, etc.) | |||
| HTTPS/SSL interception | HTTPS decoding and reconstruction with username and password available (with self-signed certificate or Sub-CA certificate available by other party) | |||
| File transfer | FTP Upload/Download, P2P File Sharing (BitTorrent, etc) | |||
| VoIP | VoIP (SIP with G.711, G.723, G.729 and iLBC Codecs) can be customized and included (optional) | |||
| Telnet | Support with Play Back | |||
| Social media | Facebook, twitter, Google+, Linkedin, etc. | |||
| Cloud service | CDR of Dropbox, Evernote | |||
| Geo-location service | Google location service, GIS Data from Facebook | |||
| Video | Youtube, etc. | |||